Extortion Fraud is Still on the Rise

Authored by Lakshya Mathur and Sriram P
McAfee Intelligence observed a huge spike in extortion email frauds over the past month. The intent of these fraudulent activities is to intimidate individuals into paying a specified amount of money as a ransom.
Figure 1 shows the number of blackmail emails received over a month recently.
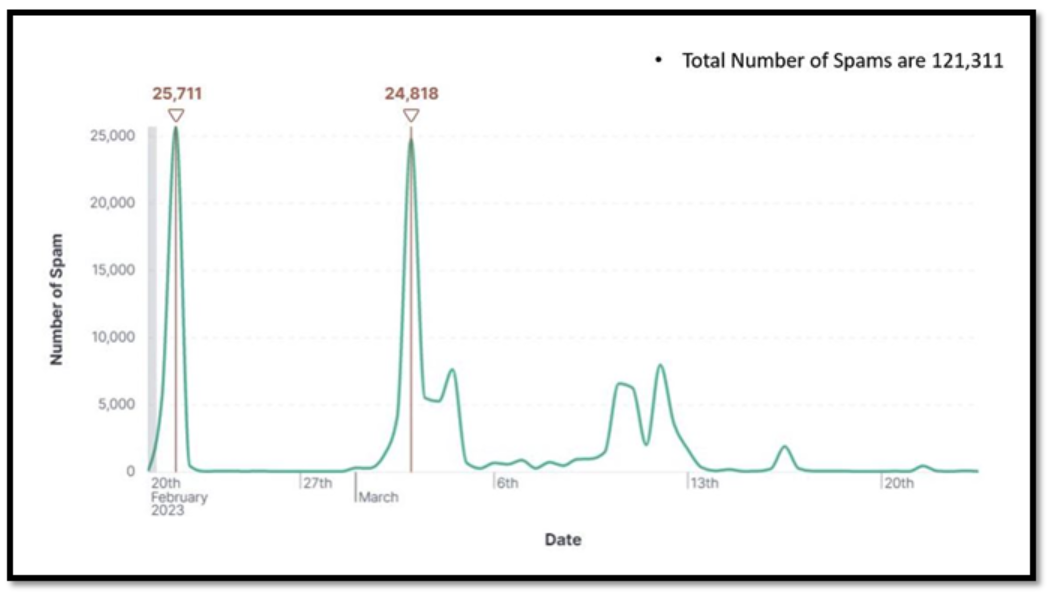
Figure 1 – Stats for 20 February 2023 – 23rd March 2023
In this blog, we’ll delve into frauds that are becoming increasingly common in the digital age. We’ll first define what these frauds are and provide examples to help readers better understand the nature of these frauds. Additionally, we’ll explore how these frauds are on the rise, highlighting the reasons behind this trend and the impact it has on individuals.
Finally, we’ll provide practical advice to help consumers protect themselves from these types of attacks. This will include a discussion of some of the most effective measures individuals can take to safeguard their personal and financial information from fraudsters.
What are Extortion Frauds?
Extortion emails are a type of scam where cybercriminals send threatening messages to individuals or organizations—demanding payment in exchange for not releasing sensitive or embarrassing information. These emails typically claim that the sender has compromising information, such as private photos or personal data, and threaten to share it with the recipient’s friends, family, or the public unless a payment is made. The payment is usually asked in the form of cryptocurrency, such as Bitcoin in the recent spam, which is difficult to trace and can be transferred quickly and anonymously. The goal of these emails is to scare the recipient into paying the demanded amount, even though there might not be any compromising information to release.
Examples of Extortion fraud
Scammers use different scareware sentiments like bad internet browsing habits, hacking for Wi-Fi, and hacking of networks because of hardware vulnerabilities. We’ll now examine various illustrations of extortion emails and analyze scammers’ strategies to intimidate victims into providing payment. By presenting various real-life examples, we can demonstrate how scammers use scareware tactics to manipulate and intimidate their victims into complying with their demands. By instilling fear, the scammers hope to provoke a sense of urgency in the victim, increasing the likelihood that they will pay the demanded ransom.
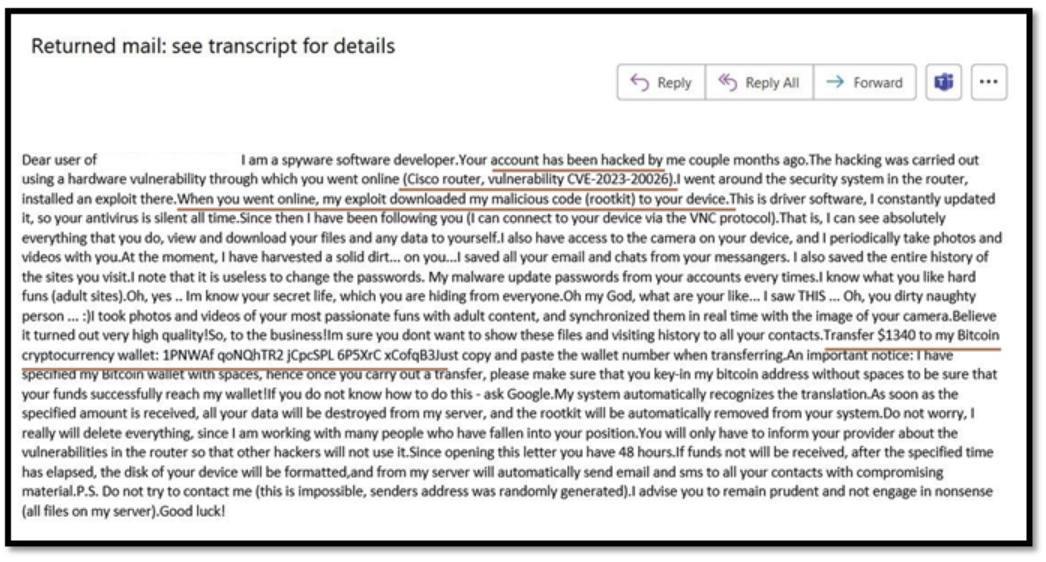
Figure 2 – Extortion fraud Example 1
Figure 2 is an illustration of a typical extortion email that scammers use to exploit their victims. In this instance, the scammer is claiming to have gained unauthorized access to the victim’s account through a security vulnerability in a Cisco router. The scammer is then threatening to expose embarrassing information about the victim unless a payment of $1,340 is made.
The payment is demanded through a Bitcoin wallet address that the scammer has provided. In this example, the scammer has obfuscated the Bitcoin wallet address by adding spaces between the characters, which is a tactic used to make it harder to track the payment. Now, let us examine another instance of extortion emails.
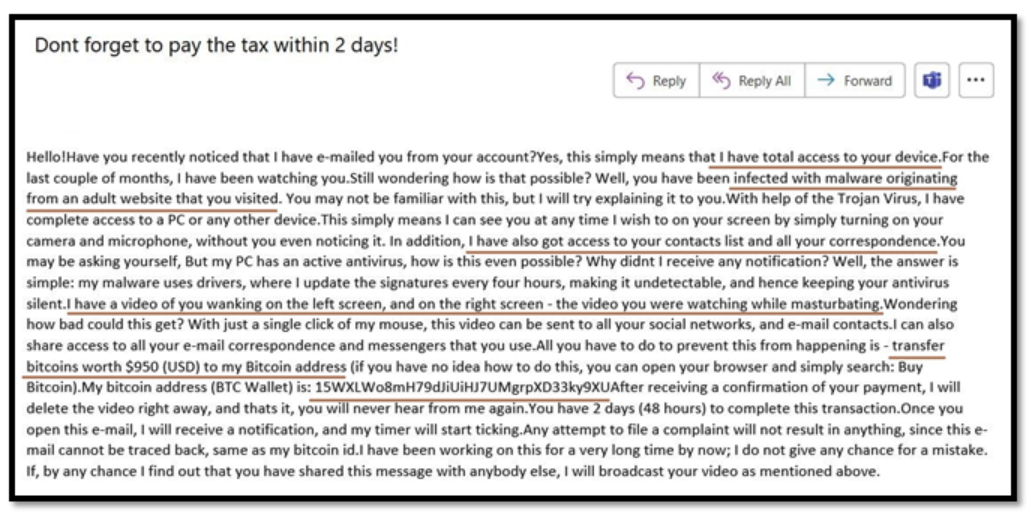
Figure 3 – Extortion fraud example 2
Figure 3 is another example of an extortion email that scammers use to trick and manipulate their victims. In this case, the attacker is claiming to have gained unauthorized access to the victim’s accounts and has deployed trojans and viruses on the victim’s system. The scammer is also blackmailing the victim by alleging that they have explicit adult content about the victim and the victim’s web browsing history. The purpose of this is to instill fear and provoke a sense of urgency in the victim.
Like the previous example, the scammer has provided a Bitcoin wallet address for the victim to make a ransom payment of $950. Additionally, the attacker has explained that the virus they’ve deployed is undetectable by antivirus software because they’ve used drivers that update the virus every few hours.
Use of Cryptocurrency
Cryptocurrency tools are the most common way these scammers ask for a ransom. They use this tactic because it is difficult to trace and can be sent quickly and anonymously to other platforms. We noticed that scammers were demanding ransom payments through Bitcoin wallets. So, we tried to gather statistics on the number of unique Bitcoin wallets we came across in the past month.
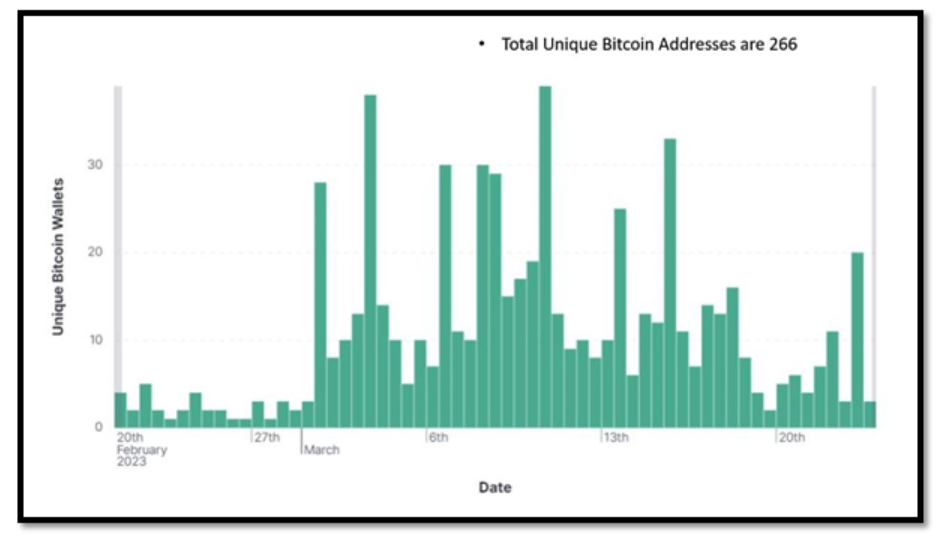
Figure 4 – Unique Bitcoin Stats for 20th February 2023 – 23rd March 2023
We checked these Bitcoin addresses to see what their transactions activities are and their reputation on the blockchain and Bitcoin abuse database. Below are some snapshots of the transaction of these addresses.
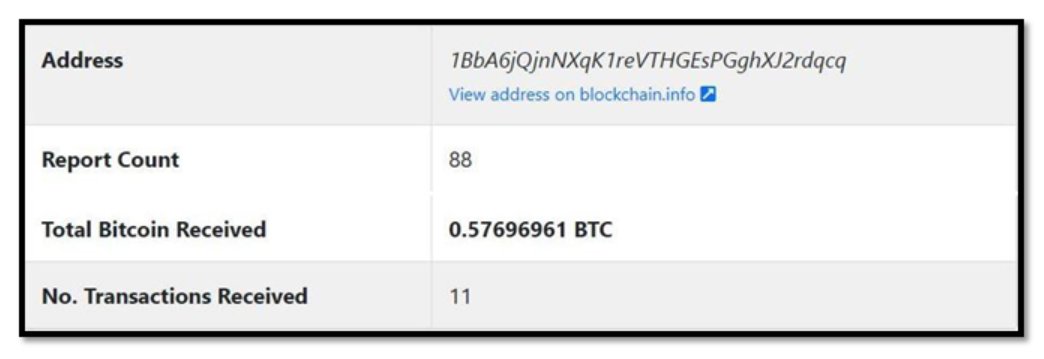
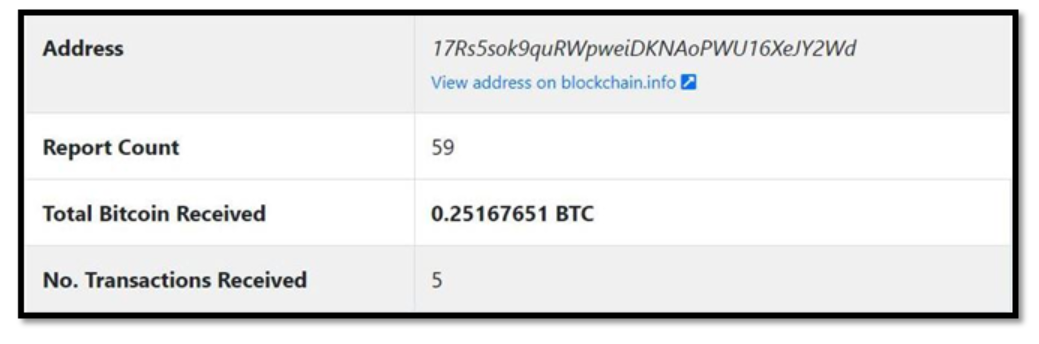
Figure 5 – Bitcoin received, and abuse report count for Bitcoin address
As illustrated in Figure 5, it is clear that the Bitcoin addresses mentioned in these extortion emails have numerous abuse reports against them. Additionally, some ransom payments have been received through these addresses. Our intelligence also collected weekly trends on how much money they had within them.
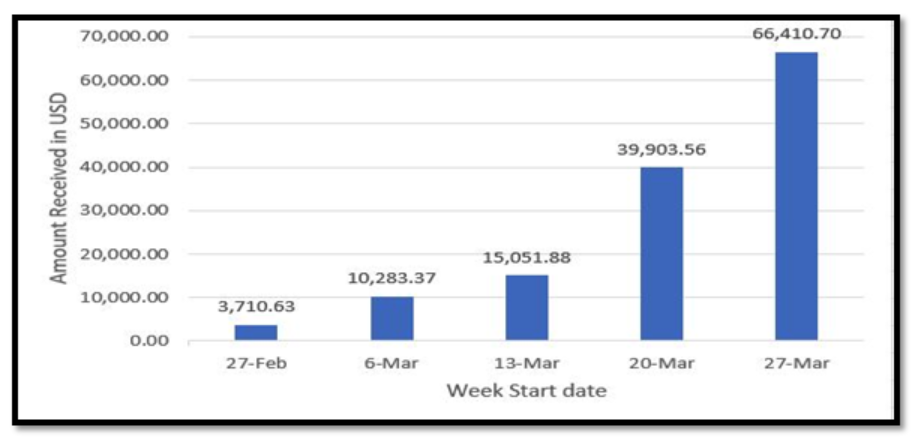
Figure 6 – Total Amount received (US Dollars) in that week
Figure 6 shows that the amount of money received in these Bitcoin addresses is increasing weekly. This implies that scammers are successfully extorting money from more consumers.
How to avoid these frauds?
If you receive extortion emails, follow the steps outlined below.
- Don’t make any decisions quickly and don’t panic. If you panic that will be a win for these scammers.
- Mostly the stuff they scare you about in the mail is always false. As soon as you receive such think twice before sending payment emails, to block them and delete them.
- Try to search important keywords on your search engines, for example, if scammers are claiming to exploit Cisco router vulnerabilities search that vulnerability with keywords like ‘BTC’, ‘hack’, and some other keywords from the email, and you will find many results which will help you to understand that the scammer’s claims are only false.
- Try to discover more about the email you got, you can search for the sender’s address, the subject of the mail, or even certain paragraphs from the mail on the internet. You will surely get information on how these emails are only scareware.
- Keep yourself educated on such scams so that you can protect yourself.
- Keep your antivirus updated and do timely full scans of your machines.
- Don’t surf on questionable web pages or download illegal/cracked software.
Despite advancements in technology, extortion frauds continue to increase as seen in this blog. However, the best defense against such scams is to remain calm, and informed, and to make others aware of such frauds. By following the steps mentioned above, such as not responding to or paying any ransom demands, keeping your system and software updated, using strong passwords, and being wary of unusual emails or links, you can protect yourself from falling victim to these frauds. It is important to stay vigilant and to report any questionable activity to the appropriate authorities. By taking these precautions, you can help prevent yourself and others from becoming victims of extortion fraud.
The post Extortion Fraud is Still on the Rise appeared first on McAfee Blog.
